אמרת2024
- 36 שאלות
- 38 תגובות
- 0% הושלמו
- equalizer סטטיסטיקות
- share שתף
Discuss, Learn and be Happy דיון בשאלות
help
brightness_4
brightness_7
format_textdirection_r_to_l
format_textdirection_l_to_r
נתונה הרשת הארגונית הבאה: כמתואר בתרשים במחלקת E ישנם 3 מחשבים שעליהם עובדים משתמשים (A, B, C) ושרת קבצים D. על מחלקת E אמונה חומת האש בשם FW. בנוסף בארגון קיים שרת WEB בשם F. הניחו ש-FW הוא stateless packet filter וזוהי ה-rules table שלה בשם T. איש האבטחה בארגון, הציע למחוק מטבלה T את חוק מספר 1 בטענה שבכל מקרה אי אפשר לגשת לשרת D שכן בשורה 4 יתרחש DROP מכל מחשב שיבקש לגשת. האם הוא צודק?
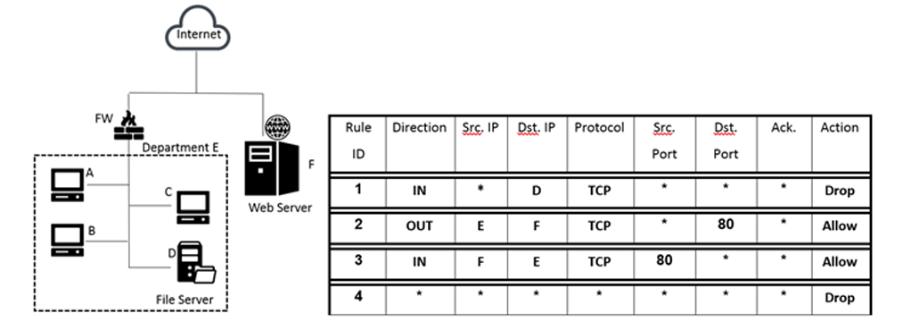
1
| done |
מיין לפי
מוניטין: 126
Line 3 in the firewall rules allows incoming TCP connections from the web server (F) to department E (including the file server D) on port 80. This means that the web server (F) can access server D, contradicting the security person's claim that access to server D is entirely blocked by line 4.
איזה מהבאים לא נבדק בדר"כ במהלך Static Analysis?
1
| done | ||
מיין לפי
מוניטין: 126
Static Analysis is a technique used to analyze a program or a file without executing it. It usually involves examining the code, structure, and other static properties.
Strings, File metadata, Exports, and Imports are typically checked during static analysis because they can be retrieved without running the file:
Strings can reveal information embedded in the file.
File metadata (such as timestamps, author information, etc.) can provide insights about the file's origin or modification history.
Exports and Imports are crucial for understanding the functions or libraries the program is interacting with.
Executed commands, however, are not typically analyzed during static analysis because they require the program to be run. Instead, executed commands are often captured during Dynamic Analysis, which involves observing the program in execution.
Thus, executed commands are not typically part of static analysis.
מה הסיבוכיות ריצה וזיכרון של התקפת search exhaustive על מערכת קריפטוגרפית 4-DES (מערכת שמפעילה ארבע פעמים את אלגוריתם DES)?
1
| done | ||
מיין לפי
מוניטין: 126
Explanation:
DES (Data Encryption Standard) uses a 56-bit key, so the complexity of a brute-force attack (exhaustive search) on single DES is 2^56
DES means running DES four times, which increases the complexity because it increases the key size to 4 *56 = 224 bits
Therefore, the running complexity of an exhaustive search on a 4-DES system is O(2^224), s you need to search through all possible combinations of a 224-bit key.
(The memory complexity is O(2^1
because the memory required for a brute-force attack doesn’t scale with the key size—it generally only requires storing a few intermediate values at any given time. A brute-force attack is not memory-intensive, unlike attacks such as meet-in-the-middle that require more memory.
מה הבאים מהווה פגיעות Vulnerability?
1
| done | ||
מיין לפי
מוניטין: 126
Explanation:
A company that allows employees to work in the middle of the night: This is not inherently a vulnerability. It could pose a risk if it is not managed properly (e.g., if employees are not monitored or if access controls are weaker), but in itself, it doesn't constitute a vulnerability.
Saving classified documents on unmarked mobile devices: This is a vulnerability because unmarked mobile devices can be easily lost, stolen, or misused, leading to a potential data breach. The lack of security measures around sensitive information presents a security flaw.
Failure to check input in functions: This is a vulnerability that could lead to various exploits such as injection attacks (SQL injection, command injection, etc.), buffer overflows, or other issues. Input validation is crucial for security.
IP-SEC המשתמש במצב tunnel מגן על:
1
| done | ||
מיין לפי
מוניטין: 126
:The correct answer is
The entire IP packet
Explanation:
In IPSec Tunnel Mode, the entire original IP packet (both the header and the payload) is encapsulated and protected by IPSec. A new IP header is added to the packet for routing purposes, while the original packet is encrypted and authenticated, providing confidentiality, integrity, and authenticity for the entire packet.
Payload only: This describes Transport Mode, not Tunnel Mode.
Header only: IPSec Tunnel Mode protects both the header and the payload, not just the header.
No answer is correct: This is incorrect because Tunnel Mode indeed protects the entire IP packet.
נתונים ארבעה מקטעי קוד. איזה מקטעי הקוד הבאים חשוף למתקף Buffer Overflow? (התקבלו שתי תשובות)

1
| done | ||
| done |
מיין לפי
מוניטין: 126
הסבר עבור קטע הקוד הראשון:
This C code is vulnerable to a Buffer Overflow attack because it uses the gets() function. The gets() function does not perform any boundary checks and can read an arbitrary amount of input, potentially overflowing the buffer (which is only 64 bytes). This can lead to a buffer overflow if the input exceeds the buffer's allocated size.
מוניטין: 126
עבור קטע הקוד הרביעי, אני לא כל כך בטוח מדוע זה פגיע אך זו התשובה של GPT:
Even though the code uses fgets(), which is much safer than gets(), the lecturer might have flagged this code segment because:
Caution with Boundaries: When using fgets(), it's good practice to leave room for the null terminator, but the final \0 check and truncation are handled in a somewhat redundant way here. This can sometimes cause confusion about whether or not the input is fully safe.
Potential Vulnerability in Later Code: The data collected in this function (in the log array) is passed into logMessage(). If that function doesn’t handle the input safely (for instance, by using gets()), it opens the possibility for a buffer overflow. Without seeing the full context of logMessage(), the code may be flagged as potentially risky.
מוניטין: 126
Input Limitation: If the input is exactly 127 characters (or more), fgets() will stop reading, and the input might be truncated. This may not cause an immediate buffer overflow but could lead to unexpected behavior. If the programmer expects that entire input strings will be read, this truncation might not be handled well elsewhere in the code.
מה נכון לגבי חתימה דיגיטלית?
1
| done | ||
מיין לפי
מוניטין: 126
The data is hashed, and the hash is encrypted with the sender's private key to create a digital signature.
Verification: The recipient uses the sender's public key to decrypt the signature. If the decrypted hash matches the hash of the data, the signature is verified, meaning the message hasn't been altered and the sender's identity is confirmed.
מה נכון לגבי Circuit level proxy?
1
| done |
מיין לפי
מוניטין: 126
The correct answer is:
Hides the internal IP addresses and thus provides additional protection.
Explanation:
Circuit Level Proxy: It operates at the Session Layer (Layer 5) of the OSI model. Circuit level proxies do not inspect the content of the traffic itself; instead, they ensure that the packet flow between internal and external networks is valid. They mainly focus on creating and maintaining a connection between the client and server after initial approval.
Hiding Internal IP Addresses: Circuit level proxies typically hide the internal IP addresses by creating a session between the internal client and the external server. This helps to mask internal network information from the external world, providing additional protection by preventing external entities from knowing the details of the internal network.
Other options like content analysis and application-level traffic inspection refer to Application Layer proxies (such as web proxies), which operate at a different layer and provide different functionalities.
בחרו את הזוג שמייצג את הצירוף הבא: (1) אלגוריתם הצפנה סימטרית המבוססת על רשת פייסטל, (2) אלגוריתם הצפנה אסימטרית שמשתמשת במפתח פומבי:
1
| done | ||
מיין לפי






